Using LDAP registry on Mobile Foundation deployed on IBM Cloud Private (ICP)
Krishna K Chandrasekar, Yathendra Prasad May 09, 2019
MobileFirst_Foundation IBM_Cloud_Private IKS Customization LDAP Mobile_Foundation on-premiseWhen Mobile Foundation (MFP) Server Helm chart is deployed on IBM Cloud Private it uses basicRegistry along with various other configuration details. This user registry is good enough for basic development and testing environments, but for production scenarios LDAP registry is used.
This blog focuses on how to use Apache Directory Server as an LDAP registry against the Mobile Foundation server that is deployed on IBM Cloud Private (or IBM Cloud Kubernetes Service, IKS).
This blog post focuses on how to use the Apache Directory Server as an LDAP Registry with Mobile Foundation Server on ICP and assumes the following:
a) User has an MFP setup on IBM Cloud Private loaded with IBM Mobile Foundation Passport Advantage Archive on ICP.
b) User has the knowledge of LDAP Registry.
Procedure
- [Optional] Make sure the configured LDAP Registry works with MFP devkit and the MFP console is accessible to the ldap users instead of basic users that comes Out-of-box.
-
From the Apache Directory Studio, make sure that the LDAP is configured correctly. For instance this article uses the following ldap setting.
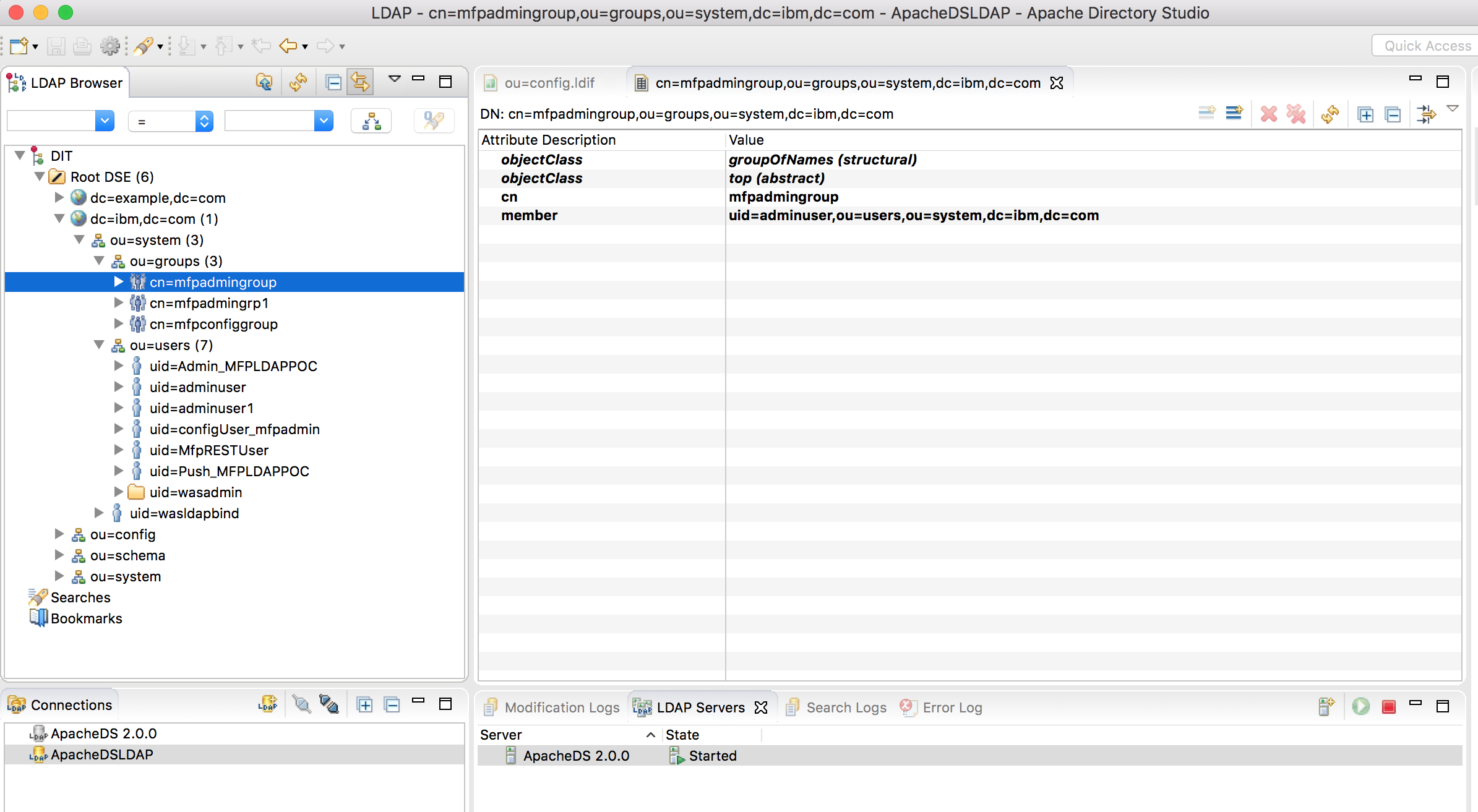
-
Create registry.xml as follows
[root@mymachine ~]# mkdir -p usr-mfpf-server/config [root@mymachine ~]# cd usr-mfpf-server/configThis creates the following directory structure that can be used to customize the image on the ICP for modifying the registry.xml
icp-kubernetes/usr-mfpf-server ├── config │ └── registry.xml -
Create a file registry.xml with LDAP registry configuration as follows:
<?xml version="1.0" encoding="UTF-8"?> <server> <featureManager> <feature>appSecurity-2.0</feature> <feature>ldapRegistry-3.0</feature> </featureManager> <ldapRegistry id="ldap" host="hostname" port="10389" ignoreCase="true" baseDN="dc=ibm,dc=com" ldapType="Custom" recursiveSearch="true" sslEnabled="false" bindDN="uid=admin,ou=system" bindPassword="secret"> <customFilters userFilter="(&(uid=%v)(objectclass=inetOrgPerson))" groupFilter="(&(member=uid=%v (objectclass=groupOfNames))" userIdMap="*:uid" groupIdMap="*:cn" groupMemberIdMap="ibm-allGroups:member;ibm-allGroups:uniqueMember;groupOfUniqueNames:uniqueMember;groupOfNames:member"/> <group name="mfpadmingroup"> <member name="adminuser"/> </group> <group name="mfpconfiggroup"> <member name="configUser_mfpadmin"/> </group> <member name="MfpRESTUser"/> <member name="Push_MFPLDAPPOC"/> <member name="Admin_MFPLDAPPOC"/> </ldapRegistry> </server>Note: Make sure the right user and group details are used according to your own LDAP server settings.
-
Create a Dockerfile to overwrite registry.xml as follows
FROM mycluster.icp:8500/default/mfpf-server:1.0.0.1 COPY registry.xml /opt/ibm/wlp/usr/servers/config/registry.xml -
Build docker image with a new tag name (say 1.0.0.2)
[root@mymachine ~]# docker build . -t mfpf-server:1.0.0.2This updates the existing mfp-server docker image with the customized registry.xml.
-
Log in to the ICP cluster and docker registry via commandline:
[root@mymachine ~]# bx pr login -a https://<icp_cluster_ip>:8443 --skip-ssl-validation -u admin -p xxxx -c <mycluster-account> [root@mymachine ~]# docker login mycluster.icp:8500 -u admin -p xxxx -
Push the new image to the ICP container repository as follows:
[root@mymachine ~]# docker tag mfpf-server:1.0.0.2 mycluster.icp:8500/default/mfpf-server:1.0.0.2 [root@mymachine ~]# docker push mycluster.icp:8500/default/mfpf-server:1.0.0.2 -
Check the available Mobile Foundation Server deployment on Kubernetes as follows:
kubectl get deployments NAME DESIRED CURRENT UP-TO-DATE AVAILABLE AGE mfpserver-ibm-mfpf-server-prod 2 2 2 2 5d -
Now update Mobile Foundation Server kubernetes deployment mfpserver-ibm-mfpf-server-prod to use the customized image.
kubectl edit deployments mfpserver-ibm-mfpf-server-prod -
Replace - image: mycluster.icp:8500/default/mfpf-server:1.0.0.1 with - image: mycluster.icp:8500/default/mfpf-server:1.0.0.2
-
Once the image is updated in the kube configuration, the mfp server pods are deleted and recreated automatically using the new configuration. Make sure that all the pods are running and ready using the command below:
kubectl get pods - Log in to the ICP Console with one of the configured LDAP user (here adminuser) and make sure the login is successful and all the services are up and running from the Mobile First Server Operations Console.
The above set of instructions are applicable for using any other LDAP servers like IBM Directory Server, Microsoft Active Directory Server etc.
Configuring On-premise MobileFirst with LDAP Registry
In case of OnPrem MobileFirst Installation with Liberty as the application server, do the following changes to your Liberty server.xml.
-
Add <feature>ldapRegistry-3.0</feature> under **
** to enable LDAP communication between MFP running Liberty server and LDAP server. -
Add ldapRegistry configuration and the sample is as follows. Attributes like baseDN, bindDN, bindPassword and user/group values might vary according to your LDAP configuration.
<ldapRegistry id="ldap" host="hostname" port="10389" ignoreCase="true" baseDN="dc=ibm,dc=com" ldapType="Custom" recursiveSearch="true" sslEnabled="false" bindDN="uid=admin,ou=system" bindPassword="secret"> <customFilters userFilter="(&(uid=%v)(objectclass=inetOrgPerson))" groupFilter="(&(member=uid=%v (objectclass=groupOfNames))" userIdMap="*:uid" groupIdMap="*:cn" groupMemberIdMap="ibm-allGroups:member;ibm-allGroups:uniqueMember;groupOfUniqueNames:uniqueMember;groupOfNames:member"/> <group name="mfpadmingroup"> <member name="adminuser"/> </group> <group name="mfpconfiggroup"> <member name="configUser_mfpadmin"/> </group> <member name="MfpRESTUser"/> <member name="Push_MFPLDAPPOC"/> <member name="Admin_MFPLDAPPOC"/> </ldapRegistry> -
Comment out <basicregistry> entry and ensure below jndi properties are set to correct values.
<jndiEntry jndiName="mfp.admin.jmx.user" value='"MfpRESTUser"'/> <jndiEntry jndiName="mfp.admin.jmx.pwd" value='"restuser"'/> <jndiEntry jndiName="mfpadmin/mfp.config.service.password" value='"configuser"'/> <jndiEntry jndiName="mfpadmin/mfp.config.service.user" value='"configUser_mfpadmin"'/> -
Make sure you configure <security-role> of an application by rightly adding appropriate users and group that has been defined in the above step. Below is the sample to configure <security-role> of an MobileFirst Admin Service Application.
<application id="mfpadmin" name="mfpadmin" location="mfp-admin-service.war" type="war"> <application-bnd> <security-role name="mfpadmin"> <group name="mfpadmingroup"/> <user name="adminuser"/> </security-role> <security-role name="mfpdeployer"> <group name="mfpconfiggroup"/> <user name="configUser_mfpadmin"/> </security-role> <security-role name="mfpmonitor"> </security-role> <security-role name="mfpoperator"> </security-role> </application-bnd> <classloader delegation="parentLast"> </classloader> </application>
For more details on Configuring LDAP user registries in Liberty, refer to the documentation
Inclusive terminology note: The Mobile First Platform team is making changes to support the IBM® initiative to replace racially biased and other discriminatory language in our code and content with more inclusive language. While IBM values the use of inclusive language, terms that are outside of IBM's direct influence are sometimes required for the sake of maintaining user understanding. As other industry leaders join IBM in embracing the use of inclusive language, IBM will continue to update the documentation to reflect those changes.




