Application Authenticity
improve this page | report issueOverview
To properly secure your application, enable the predefined MobileFirst application-authenticity security check (appAuthenticity). When enabled, this check validates the authenticity of the application before providing it with any services. Applications in production environment should have this feature enabled.
To enable application authenticity, you can either follow the on-screen instructions in the MobileFirst Operations Console → [your-application] → Authenticity, or review the information below.
Availability
- Application authenticity is available in all supported platforms (iOS, watchOS, Android, Windows 8.1 Universal, Windows 10 UWP) in both Cordova and native applications.
Jump to:
- Application Authenticity flow
- Enabling Application Authenticity
- Configuring Application Authenticity
- Build Time Secret (BTS)
- Troubleshooting
Application Authenticity Flow
The application-authenticity security check is run during the application’s registration to MobileFirst Server, which occurs the first time an instance of the application attempts to connect to the server. By default the authenticity check does not run again.
Once app authenticity is enabled and if customer needs to introduce any changes in their application, then the application version needs to be upgraded.
See Configuring application authenticity to learn how to customize this behavior.
Enabling Application Authenticity
For application authenticity to be enabled in your application:
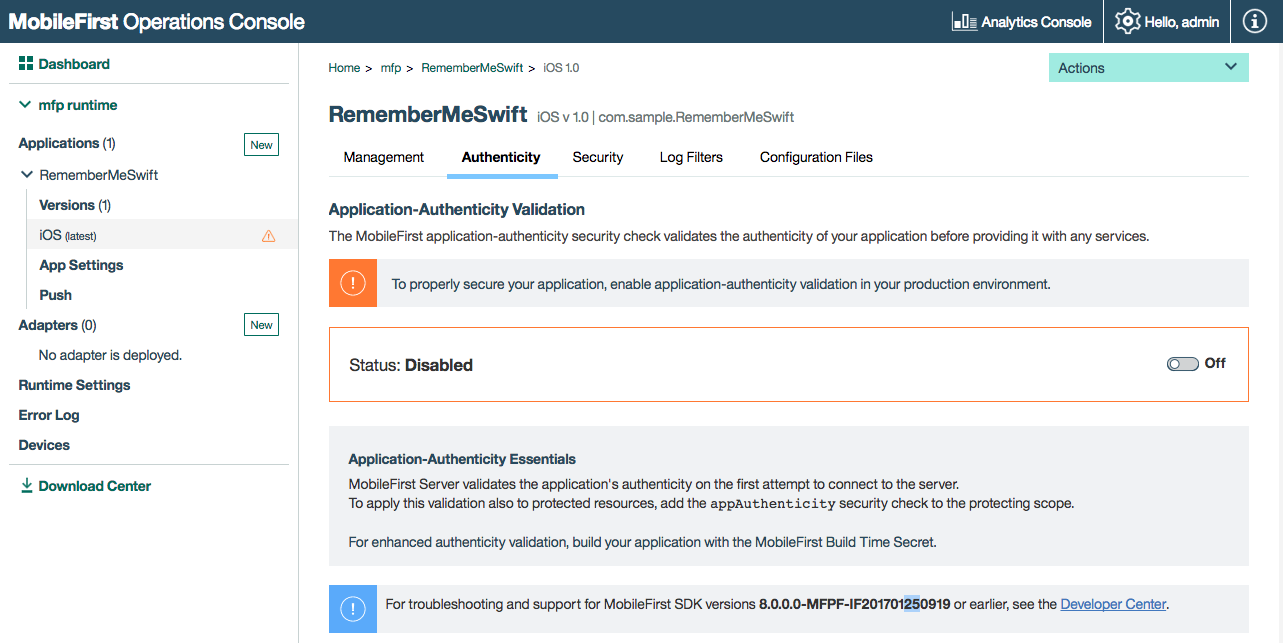
- Open the MobileFirst Operations Console in your favorite browser.
- Select your application from the navigation sidebar and click on the Authenticity menu item.
- Toggle the On/Off button in the Status box.
MobileFirst Server validates the application’s authenticity on the first attempt to connect to the server. To apply this validation also to protected resources, add the appAuthenticity security check to the protecting scope.
Disabling Application Authenticity
Some changes to the application during development might cause it to fail the authenticity validation. Accordingly, it is recommended to disable application authenticity during the development process. Applications in production environment should have this feature enabled.
To disable application authenticity, toggle back the On/Off button in the Status box.
Configuring Application Authenticity
By default, Application Authenticity is checked only during client registration. However, just like any other security check, you can decide to protect your application or resources with the appAuthenticity security check from the console, following the instructions under Protecting resources.
You can configure the predefined application-authenticity security check with the following property:
expirationSec: Defaults to 3600 seconds / 1 hour. Defines the duration until the authenticity token expires.
After an authenticity check has completed, it does not occur again until the token has expired based on the set value.
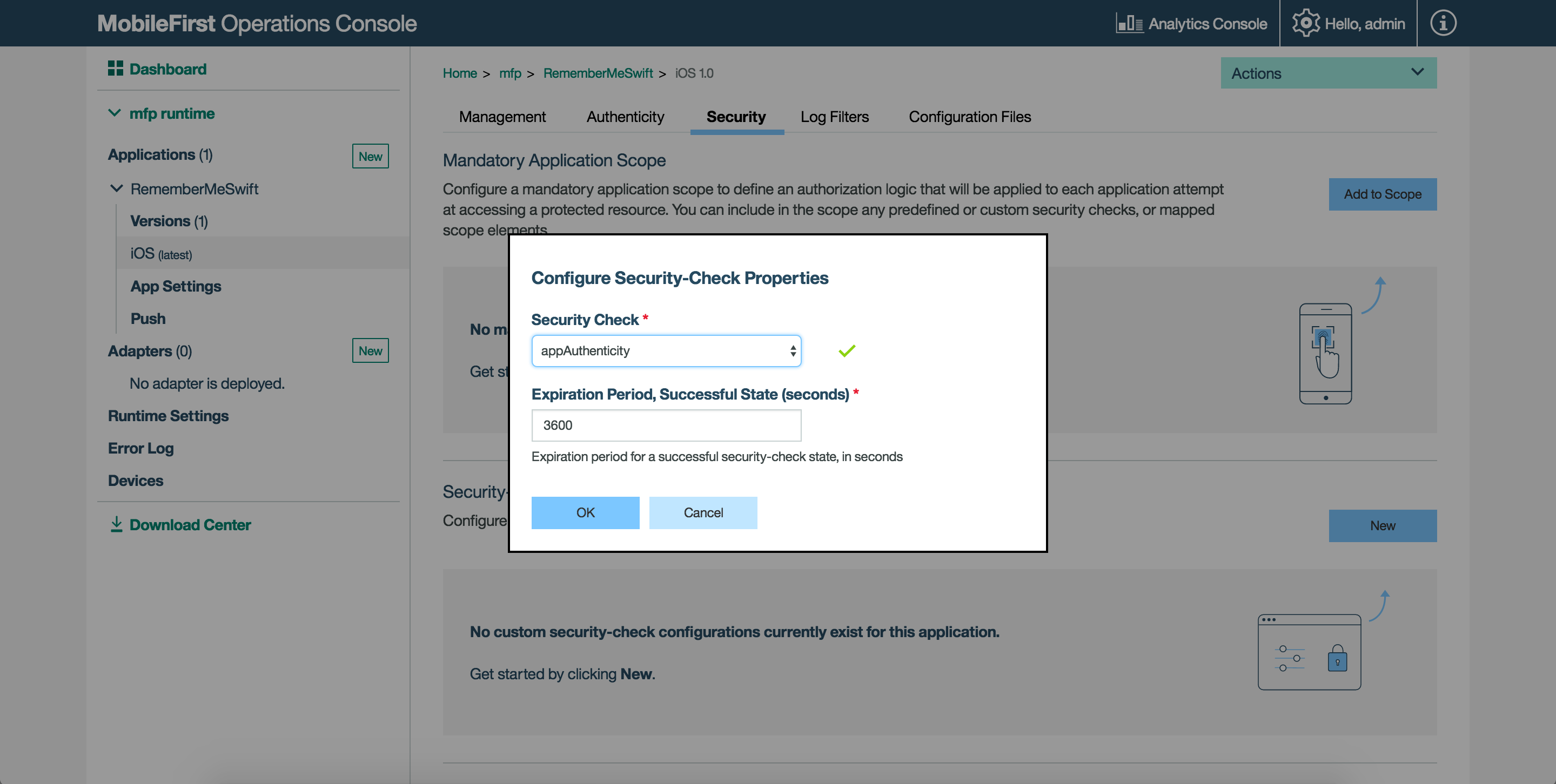
To configure the expirationSec property:
-
Load the MobileFirst Operations Console, navigate to [your application] → Security → Security-Check Configurations, and click on New.
-
Search for the
appAuthenticityscope element. -
Set a new value in seconds.
Build Time Secret (BTS)
The Build Time Secret (BTS) is an optional tool to enhance authenticity validation, for iOS and watchOS applications only. The tool injects the application with a secret determined at build time, which is later used in the authenticity validation process.
The BTS tool can be downloaded from the MobileFirst Operations Console → Download Center.
To use the BTS tool in Xcode:
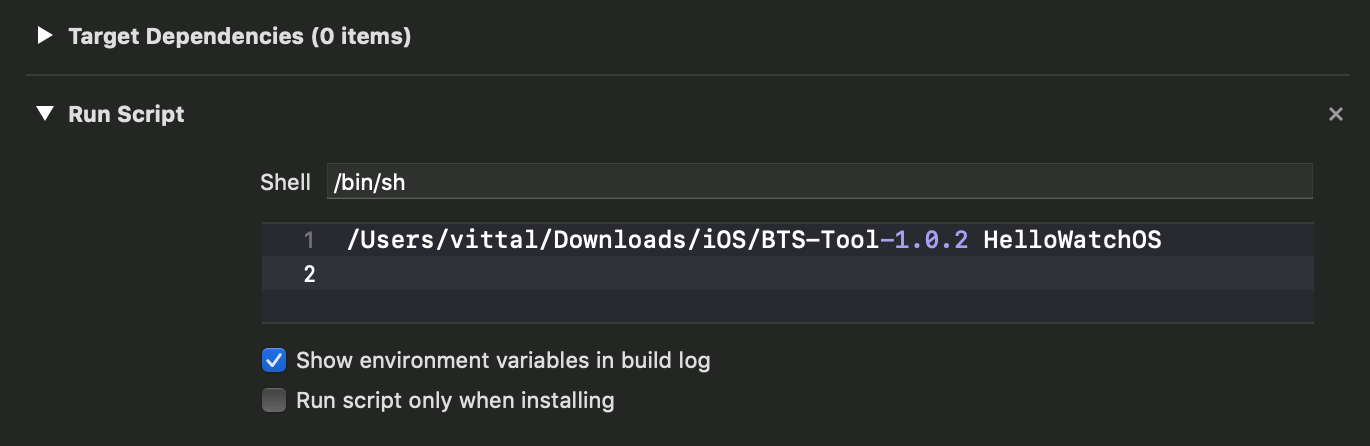
- Under the Build Phases tab click the + button and create new Run Script Phase.
- Copy the path of BTS Tool and paste in the new Run Script Phase you have created.
- Drag the Run Script Phase above the Compile sources phase.
- This step is required only if the application environment is watchOS. To enable BTS, developer needs to pass any swift file name, which is packaged in the watchOS extension after the BTS tool location.
For example, suppose if the watchOS extension package contains HelloWatchOS.swift file, the developer will need to pass HelloWatchOS as an argument along with the path of BTS tool.
The tool should be used when building a production version of the application.
Troubleshooting
Reset
The application authenticity algorithm uses application data and metadata in its validation. The first device to connect to the server after enabling application authenticity provides a “fingerprint” of the application, containing some of this data.
It is possible to reset this fingerprint, providing the algorithm with new data. This could be useful during development (for example after changing the application in Xcode). To reset the fingerprint, use the reset command from the mfpadm CLI.
After resetting the fingerprint, the appAuthenticity security check continues to work as before (this will be transparent to the user).
Validation Types
Mobile First Platform Foundation provides static and dynamic app authenticity for applications. These validation types differ on the algorithm and attributes used to generate app authenticity seeds. By default, when application authenticity is enabled, it uses the dynamic validation algorithm. Both the validation types ensure the security of the application. Dynamic app authenticity uses strict validations and checks for app authenticity. For static app authenticity, we use slightly relaxed algorithm, which will not use all the validation checks as used in dynamic app authenticity.
The dynamic app authenticity is configurable from MobileFirst Console. The internal algorithm takes care of generating app authenticity data based on the options chosen in console. For static app authenticity, one need to use the mfpadm CLI.
For enabling static app authenticity and to switch between validation types, use the mfpadm CLI:
mfpadm --url= --user= --passwordfile= --secure=false app version [RUNTIME] [APPNAME] [ENVIRONMENT] [VERSION] set authenticity-validation TYPE
TYPE can either be dynamic or static.
Support for SDK versions 8.0.0.0-MFPF-IF201701250919 or earlier
The dynamic and static validation types are only supported by client SDKs released in February 2017 or later. For SDK versions 8.0.0.0-MFPF-IF201701250919 or earlier, use the legacy application authenticity tool:
The application binary file must be signed by using the mfp-app-authenticity tool. Eligible binary files are: ipa for iOS, apk for Android, and appx for Windows 8.1 Universal & Windows 10 UWP.
- Download the mfp-app-authenticity tool from the MobileFirst Operations Console → Download Center.
-
Open a Command-line window and run the command:
java -jar path-to-mfp-app-authenticity.jar path-to-binary-fileFor example:
java -jar /Users/your-username/Desktop/mfp-app-authenticity.jar /Users/your-username/Desktop/MyBankApp.ipaThis command generates an
.authenticity_datafile, calledMyBankApp.authenticity_data, next to theMyBankApp.ipafile. - Upload the
.authenticity_datafile using the mfpadm CLI:app version [RUNTIME-NAME] APP-NAME ENVIRONMENT VERSION set authenticity-data FILE
Inclusive terminology note: The Mobile First Platform team is making changes to support the IBM® initiative to replace racially biased and other discriminatory language in our code and content with more inclusive language. While IBM values the use of inclusive language, terms that are outside of IBM's direct influence are sometimes required for the sake of maintaining user understanding. As other industry leaders join IBM in embracing the use of inclusive language, IBM will continue to update the documentation to reflect those changes.